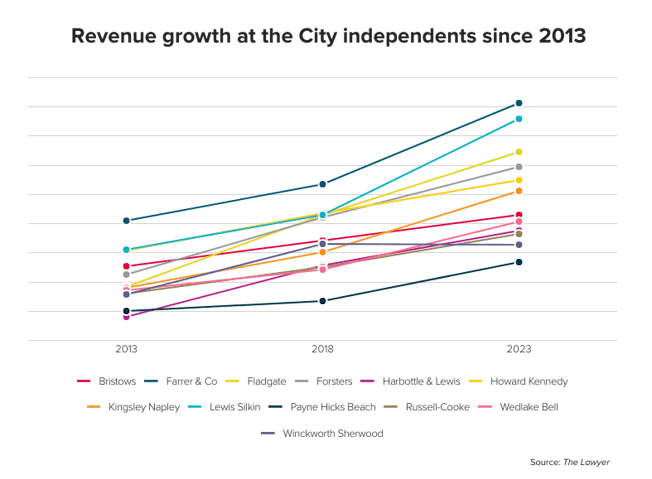
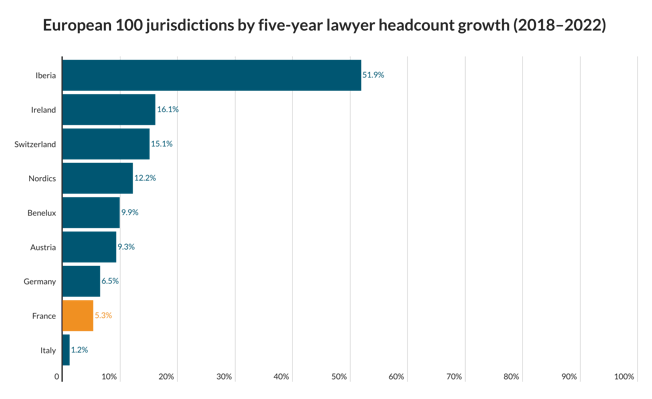
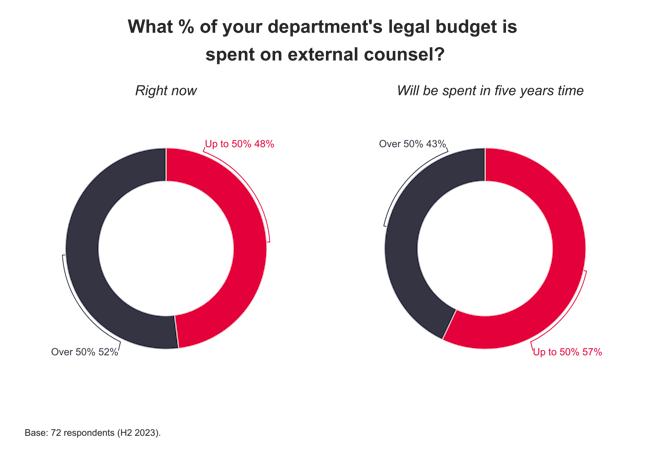
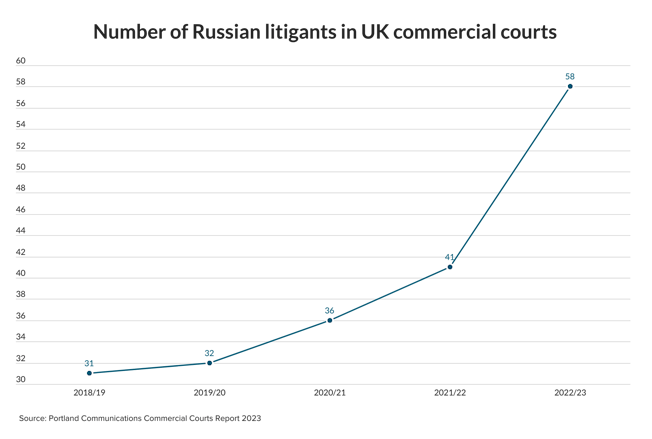
World figures
With businesses increasingly operating across international borders, Maryam Kennedy looks at how forensic accounting is keeping pace with the challenges of different regulatory regimes How many languages can you speak? Are you able to travel with 24 hours’ notice? Which of the former Soviet states have you worked in? These three crucial questions neatly encapsulate […]