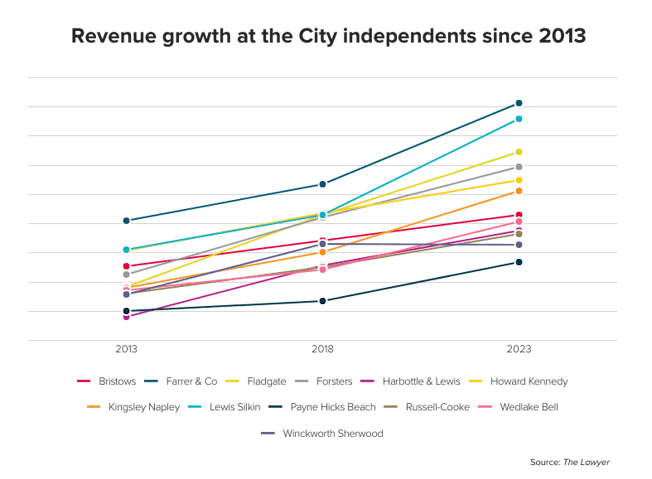
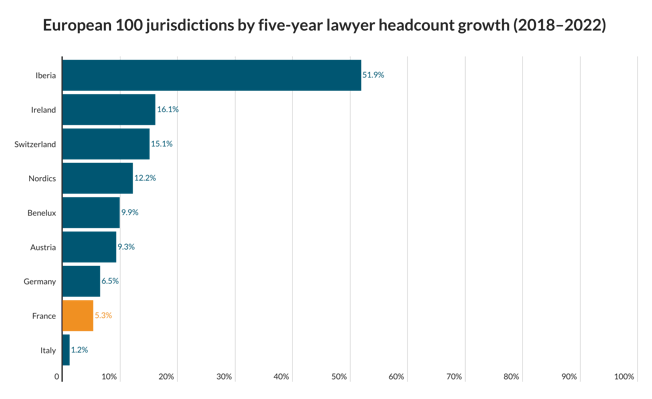
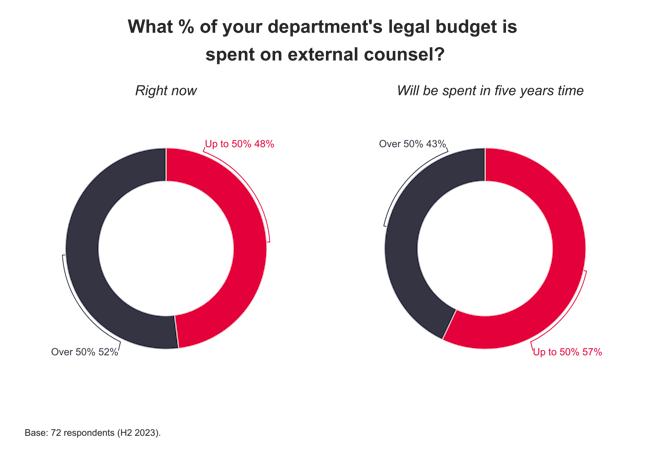
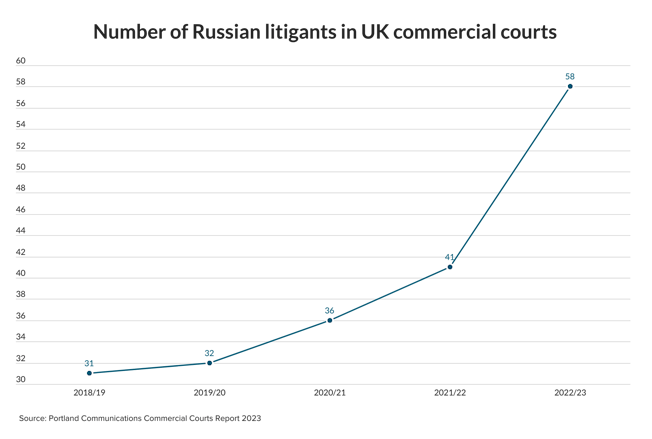
A&O, Freshfields and Uría act on Qatar Holding’s €2.1bn Iberdrola acquisition
Magic circle pair Allen & Overy (A&O) and Freshfields Bruckhaus Deringer have been joined by Spanish giant Uría Menéndez to guide Qatar Holding’s purchase of a €2.1bn stake in Iberdrola. Freshfields acted for Qatar Holding on its latest Spanish investment, with corporate partners Sarah Murphy and Bruce Embley leading in London alongside tax partner Jonathan […]