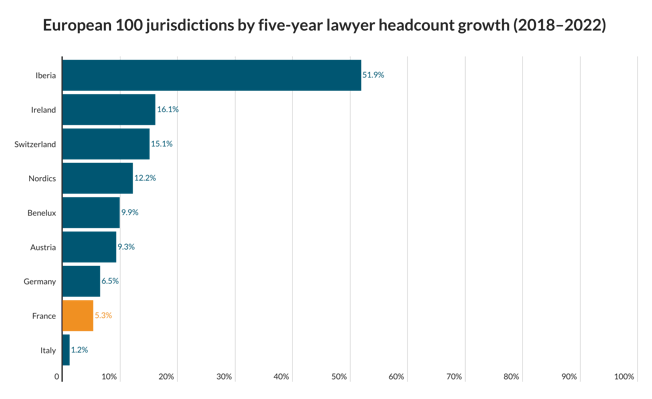
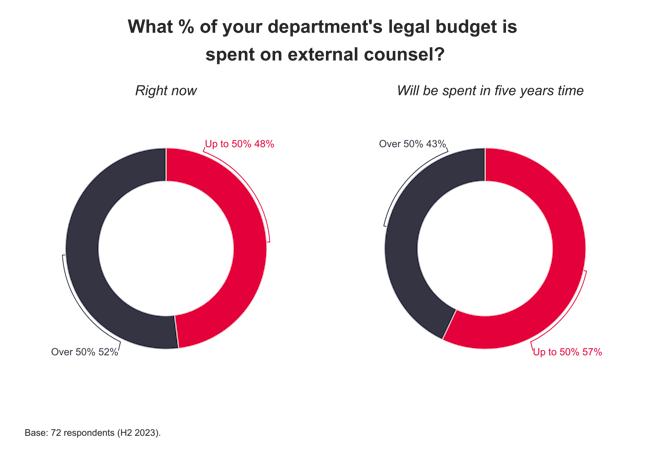
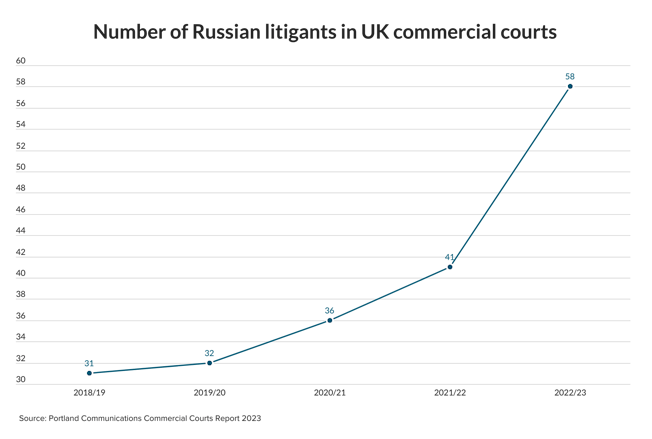
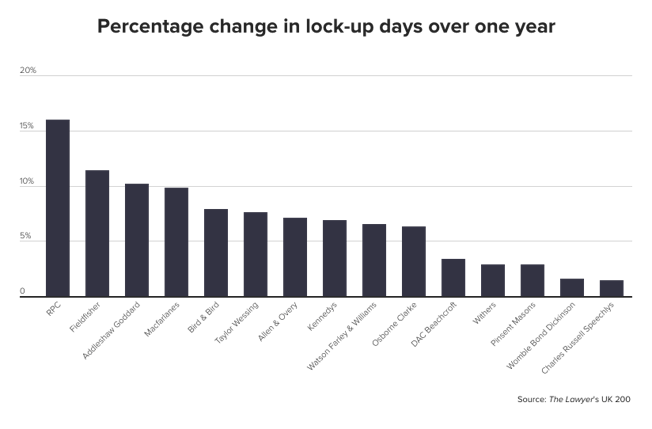
Cyber security: it’s big and it’s scary
This week’s issue is devoted to cyber security, a topic simultaneously fascinating and terrifying. Along with our lead feature, we also have an interview with the in-house team at the Information Commissioner’s Office (ICO). Our sister company Global Security Finance, a subsidiary of VB Research, has interviewed key players in the sector, which we’re also […]